LastPass Hack - Act now!
Further revelations relating to the LastPass Hack in December 2022 indicate that customers who have been using LastPass for longer are more at risk as the encryption applied to their vault has not been updated and improved over time in the way it was for new customers signing up for the service.
The key factor in protecting encrypted data from a brute force attack (guessing all possible password variations) is the number of times the data is hashed (encrypted) using an algorythm called PBKDF. In the olden days - back in the early 2000, computers were slow and passing your data through the PBKDF once was enough to consider it secure. But as computers got faster it became more viable to try to guess all possible permutations and the execution of the encryption function got quicker. So the simple answer was to run the encryption multiple times.
LastPass changed the number of times the data was hashed from 1 to 500 in 2012. Then less than a year later is was increased again to 5000 and then in February 2018 it was changed to 100,100 iterations. That means when you enter your master password to unlock your vault, your computer has to run through the PBKDF process 100,100 times before your data is available.
At least that is the theory - unfortunately it appears that a flaw in LastPass’ design means that when the default number of interations was increased, this was only applied to new customer accounts - existing customers were left using whatever was the default when they signed up.
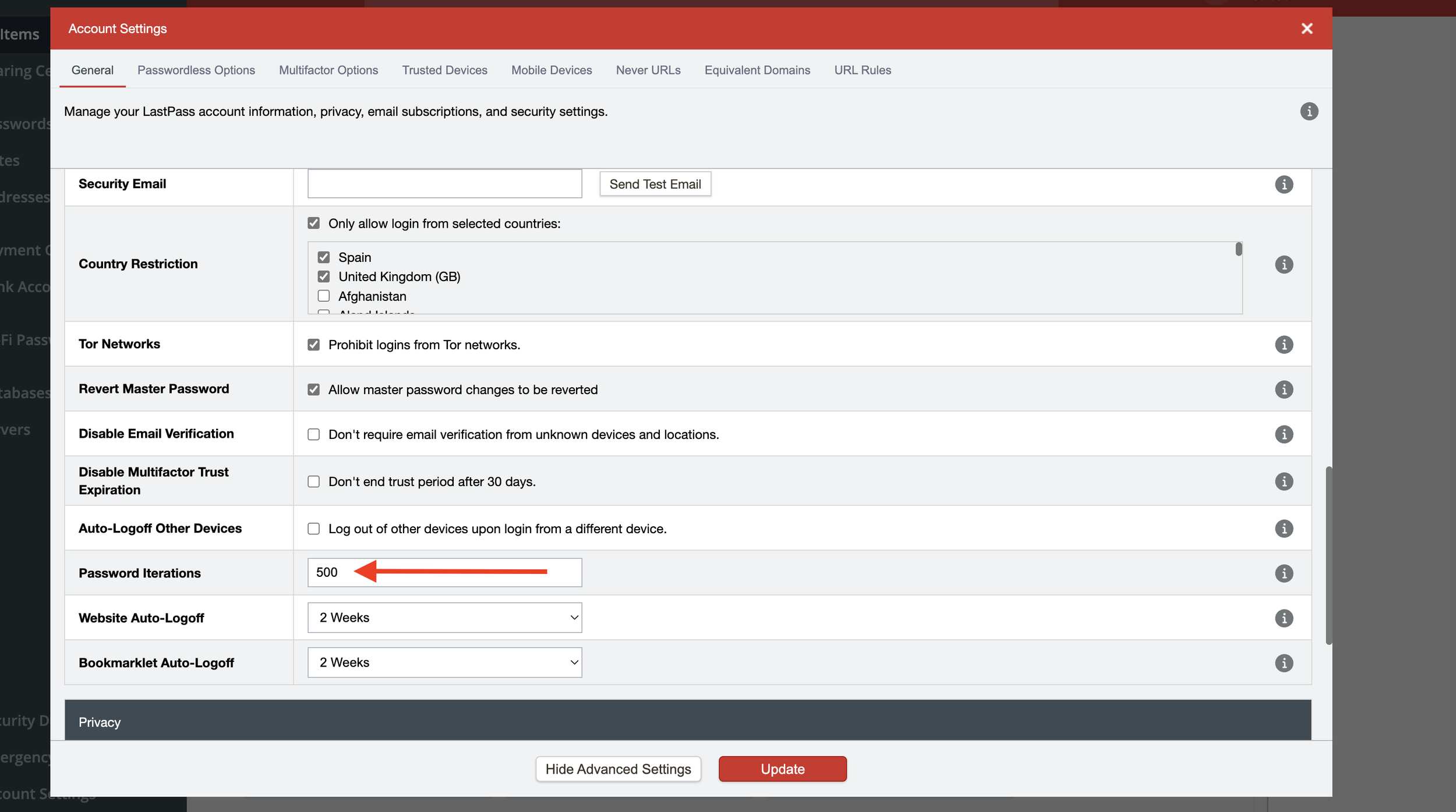
For me, as a long time LastPass customer, I checked by vault settings today the PBKDF iterations was set to 500 - just 0.005% as strong as LastPass recommends for new customers - which itself is way less than the 300,000 iterations recommended by OWASP.
You can check the password iterations settings in your LastPass vault by going to Settings > Advanced Settings and scrolling down to Password Iterations. This should be at least 100,100 but a value over 300,000 is better.
Although I had a LastPass account from history, I have been using 1Password as my main password manager for many years. 1Password offers a more secure design in that as well as using a password to secure your vault, it also uses a secret key which remains on your computer meaning that even if your password vault were to be stolen from 1Passwords servers, it can never be decrypted without the secret key which remains on your device and is never sent to 1Password.
LastPass Password Iterations - should be at least 100,100
What should LastPass customers do?
LastPass vault encryption does not work in the way you would expect - most of the information stored in the vault is actually not encrypted at all - including the URL of the website the password belongs to, it is only the passwords and usernames that are encrypted.
So the criminals that have stolen everyones LastPass vaults are able to scan every vault easily and look for bank, crypto or valuable business logins and target those accounts either to brute force guess the password (see above) or using phishing or other social engineering to trick people into revealing their vault master password allowing the criminals to access all their passwords.
We recommend the following action plan for LastPass customers
Change the Master Password on your LastPass account
Changing your password will not protect the data already stolen but it will help protect the data still in your vault. Companies that are breached are often targeted again and again so update your security today for the attack that will come tomorrow
Enable MFA on your LastPass account
Go to Account Settings > Multi-factor Options to set up an MFA device such as Google or Microsoft Authenticator
Check the Password Iterations
If your password iterations setting is below 100,100 update the setting to at least 100,100 and then you need to consider changing every password stored in your lastpass vault - or at a minimum all the high value accounts such as: email, banking, crypto wallets and gaming accounts.
Consider changing password manager
If you do decide to change password managers, you should use a different master password on your new account and at least change all the high value passwords in your vault such as: email, banking, crypto wallets and gaming accounts.
Learn more details via Steve Gibson / Security Now Podcast: https://www.grc.com/sn/sn-905-notes.pdf